Cybercrime and hacker ingenuity continue to grow at an alarming rate, which is why effective cyber security is so challenging these days. New vulnerabilities and exploits are constantly being found, with each attack more sophisticated than the last.
However, one rather rudimentary yet effective hacker tactic that has seen a recent surge in Australia is called ‘credential stuffing’, and it poses a serious threat to Australian businesses.
WHAT IS CREDENTIAL STUFFING?
Credential Stuffing is where a hacker obtains already stolen user names and passwords, then “stuffs” them into other website logins in order to gain access to sensitive and valuable data. This type of attack is emerging as a critical new data breach risk in Australia and is considered among the top threats for web and mobile applications in 2019.
In fact:
It's a frightening stat, especially considering Australia's population in comparison to the four countries that rank above us – US, India, Canada and Germany. We also don't rank in the 'Top Attack Sources' list; only the 'Top Attack Destinations' list, meaning we are hot property for international hackers.
There were more than 100 million credential stuffing attacks made in Australia in 2018. And with up to 87% of consumers reusing their passwords online, hackers have easy access to millions of credentials, often for free.
Once a hacker gains access to your accounts, they can perform a wide range of illicit actions, from data theft through to a complete account takeover. Some examples include:
- withdrawing your account balance
- transferring funds or points
- selling access to your social media, retail store and even bank accounts on the dark web
- taking multiple free trips using your Uber account
- ordering food from sites like Deliveroo
- accessing your company’s WordPress site in order to take control over it and use it in other malware distribution campaigns
WHO'S MOST AT RISK?
Small to medium sized businesses (SMEs) need to be wary the most, with the finance, retail and gaming sectors particular hot spots for hackers. SMEs often have a lower security capacity due to smaller IT budgets and staff, making them prime targets.
WHAT CAN YOU DO TO PROTECT YOUR BUSINESS?
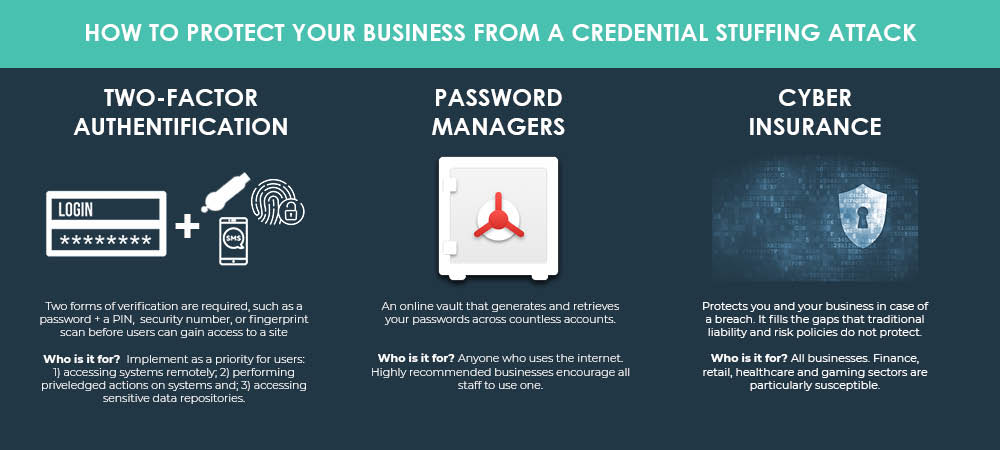
Two-factor authentication
Two-factor authentication (2FA) is one of the most effective controls an organisation can implement to prevent hackers from gaining access to sensitive information.
It also means increased productivity. With most employees now being able to work on their mobile devices outside the office, 2FA becomes particularly helpful by securing their devices so they can safely access company-owned applications, data, and shared documents without putting your company at risk.
Users simply need to provide two different authentication factors to verify themselves, such as a primary password, plus a secondary authentication like a PIN, smartcard, or fingerprint.
It is one of the top safety practices recommended by The Australian Cyber Security Centre (ACSC)
Password managers
Password managers basically generate, retrieve and keep track of unique, long and random passwords across countless accounts for you.
They’re effective, easy to use, and businesses really need to encourage staff to use them. Check the best ranked password managers in 2019.
Cyber insurance
There’s unfortunately no silver bullet that can keep your business 100% protected from a data breach, whether the attack is driven by a professional hacker on the other side of world using credential stuffing tactics, or by one of your own staff who accidentally attaches sensitive credit card information to an email. However, a tailored cyber insurance policy is there to fill all the gaps that traditional liability and risk policies do not protect, ultimately providing you and your business with peace of mind if trouble ever strikes.
Currently two-thirds of Australian SMEs operate without cyber insurance cover, leaving them vulnerable to potentially irrevocable damage. On top of the significant direct damage costs – which average around $276,000 per attack – the indirect costs to a business can also be considerable:
A cyber-attack using credential stuffing tactics could seriously compromise your financial viability in more ways than one, so a robust cyber insurance policy is a must. At the very least, it will cover risks such as financial loss arising from lost revenue, customer churn, privacy fines and legal expenses.Cyber-attacks can happen without much rhyme or reason these days, and with Australia being one of the top destinations of choice for hackers, why take the chance of putting your business, your data and your employees at risk.
Because at the end of the day, all it takes is one successful attack to bring your business to a screeching halt....or to put you out of business altogether.
DISCLAIMER:
This article is informational only and should not be construed as individual advice as it does not consider your individual needs. You should consider if the insurance is suitable for you and read the Product Disclosure Statement or policy Wording before buying insurance.


